
Proof of concept
- Published on
- body of knowledge software-engineering cyber minor · 2 min read
Proof of concept
Use cases
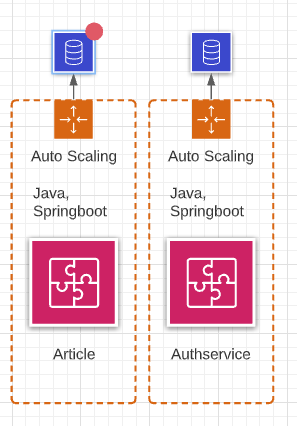
For my prototype I made two services in a microservice architecture. The fist service will serve as an auth service were the user can register and login where he then gets back a bearer token. The second service will serve as a database acces service where I can ask for a given article id.
- As a user I want to be able to lookup an article by the id, given authenticated.
- As a user I want to be able to register and get a verification
- As a user I want to be able to login given I'm verified
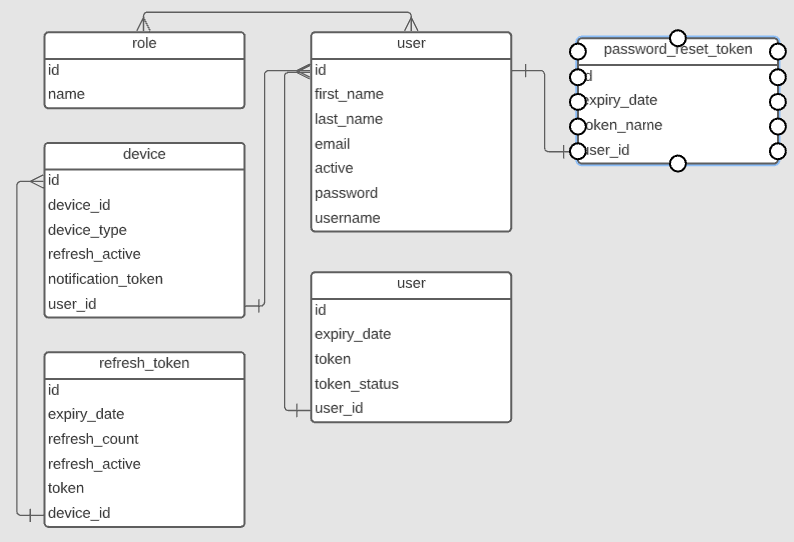
Both services use their own database
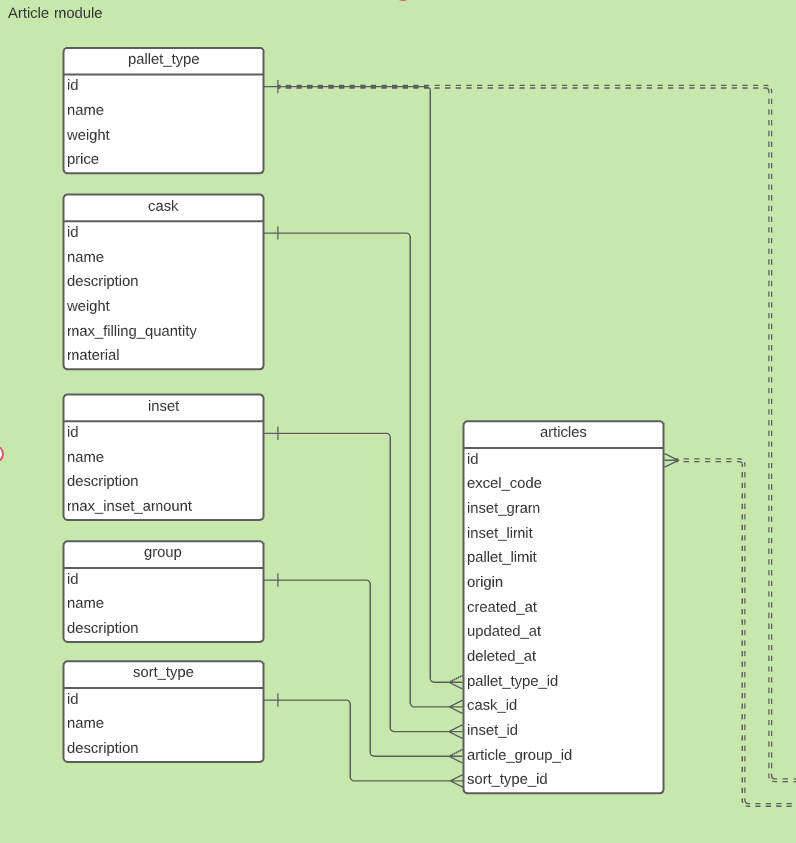
An article is bases on various connections to other tables.
| Article service | Auth service | Archtecture |
|
|
|
both services will be running on a nginx server with the two services not knowing about each other. However, they will both have an implementation for checking the jwt bearer token. Here, the two services share the same validation password.
Vulnerabilities
JWT cracking and brute forcing a password are popular methods to break into a system:
| Vulnerability | Solution |
| Brute force login when verified | Debounce / save the number of incorrectly logins block on 3 for given ip / CAPTCHA |
| Modification of bearer token and extension of rights / JWT-Cracking | encrypted password |
Links
I produced a couple proof of concepts based on project I had to develop. Multiple learning exercises have been added to the application for this idea. Because it's simply a proof of concept, a lot of features haven't been added yet. My application may be seen here:
Authentication & Authorization:
Api with hateoas hal:
Client app in Vue.js and state management:
Thank you for reading this topic about Proof of concept I hope it was interesting any feedback is always welcome. Hope to see you in the next topic,
Byee! 👋🍺
TL;DR Prototypes